Photo by Douglas Lopes on Unsplash
Portswigger Lab: Exploiting a mass assignment vulnerability
TEch Stuff Daily? Entry 2 - Hacking API's
Bismillah
Hey guys, here's another report-styled entry into the Hacking APIs part of my YouTube "TEch Stuff Daily?" Series(subscribe)
Mass Assignment Vulnerability in Checkout API.
The following mass assignment API vulnerability was found when accessing the cart allows users to assign a discount to items at purchase.
Steps To Reproduce
Tools: Burp and Browser(Firefox for me).
Add any item onto the cart - in this case let's add the leather jacket.

Access the cart and observe the response via Burp to access the cart - The Response is as shown below. (Send the request to Burp Repeater)

Attempt to order the item and capture that request as well. (Send the request to Burp Repeater)
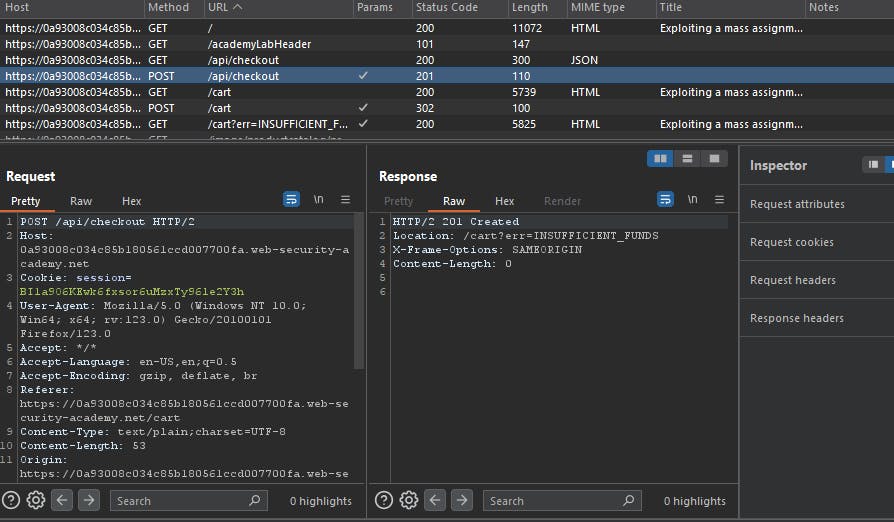
In the first request copy the "chosen_discount" key-value pair from the JSON contained in the response.

Paste this response in the JSON request to purchase the item and change the value to 100.

Attempt to order the item with the applied discount.
Bug!!

Impact
The vulnerability in question could allow users to purchase items for free, thus making huge losses for the company.
Thanks again for reading my post... Asalaam Aleykum.